February 25, 2024
I wrote a small shell script™ to automate building new Linux Kernels. I use this to build new kernels on my Debian systems:
#!/usr/bin/env bash
WORKSPACE='/home/gd/workspace'
LINUX="${WORKSPACE}/linux"
find "${WORKSPACE}" -type f \( -name 'linux-*deb' -o -name 'linux-upstream*' \) -mtime -3 -exec rm {} \;
Read More...
linux (10) kernel (5) bash (3)
December 17, 2023
My new book Hand-on Test-Driven Development Book has been published: https://tddbook.com/.

Read More...
ruby (5) rails (4) tdd (1) rspec (1)
November 26, 2023
On new Rails apps, that are not in production yet, I sometimes like to reorder my database migrations. I wrote a small Ruby script to automate things.
Read More...
rails (4) database (2)
August 2, 2023
I wanted to learn to create a dynamically-named method inside a dynamically-named class in Raku. This is what I ended up with:
#!/usr/bin/env raku
my $class-name = "MyDynamicClass";
my $method-name = "dynamic-method";
Read More...
raku (17) ruby (5) meta (1)
April 28, 2023
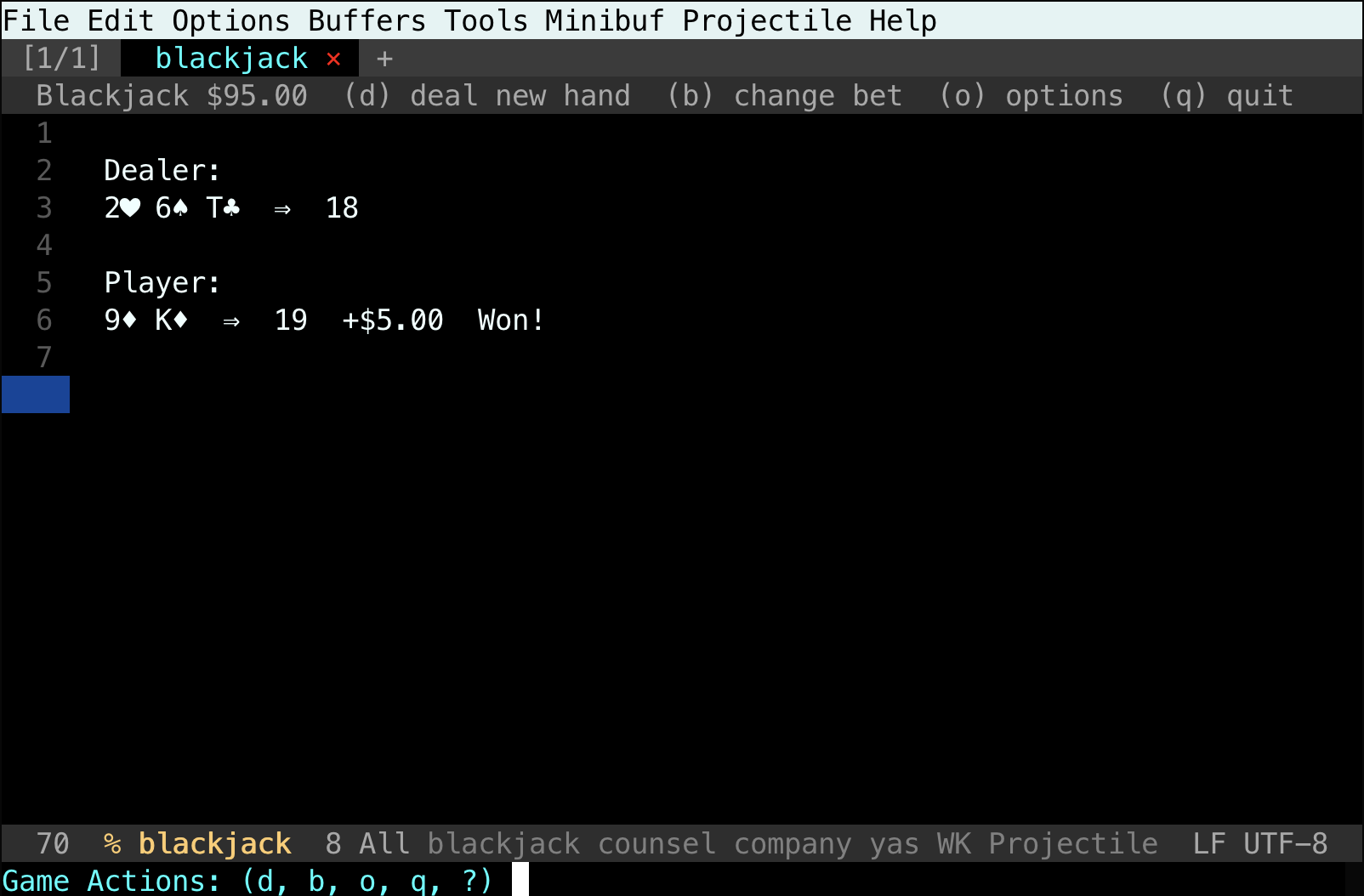
I wrote Blackjack in Elisp. It allows you to play Blackjack in your Emacs editor.
Read More...
blackjack (17) emacs (1) elisp (1)
December 25, 2022
Wow, if Django and Rails had a baby it would be Marten, the web framework written in Crystal, https://martenframework.com/.
It seems fairly feature-complete, even with only a 0.1.x version number! https://martenframework.com/docs/.
The documentation looks really solid. Clearly they just love to program and give to open-source! https://github.com/martenframework.
Read More...
crystal (2) web-framework (2)
November 27, 2022
About two days ago I built the “bookshelf” app described in the Hanami guide. Hanami is currently missing any sort of “model” layer, as well as any sort of “view” layer, as you might expect to be present from using Ruby on Rails or other MVC web frameworks.
I asked about these missing pieces on the Hanami forum and it was explained to me the missing pieces will appear in the 2.1 release, in Q1 2023, and in the meantime to please go look at two other projects, to learn by watching them being built. I looked at the two projects but saw no model or view layer code.
And as nice as I can think to say this, I don't understand how they got to a place where they decided a 2.0 version number was appropriate, given these basic components are not present, not even in some very basic form. Hanami presently seems more like a 0.5 version framework to me.
The Hanami homepage currently contains the words "full-featured". I have no idea why they would say that. "2.0" implies to me a second major version of an already completely fleshed-out framework. ¯\_(ツ)_/¯
I stopped looking at it for now. I don't want to invent all the missing pieces only to have my code become obsolete in 6 months.
Read More...
web-framework (2) hanami (1) mvc (1)
October 10, 2022
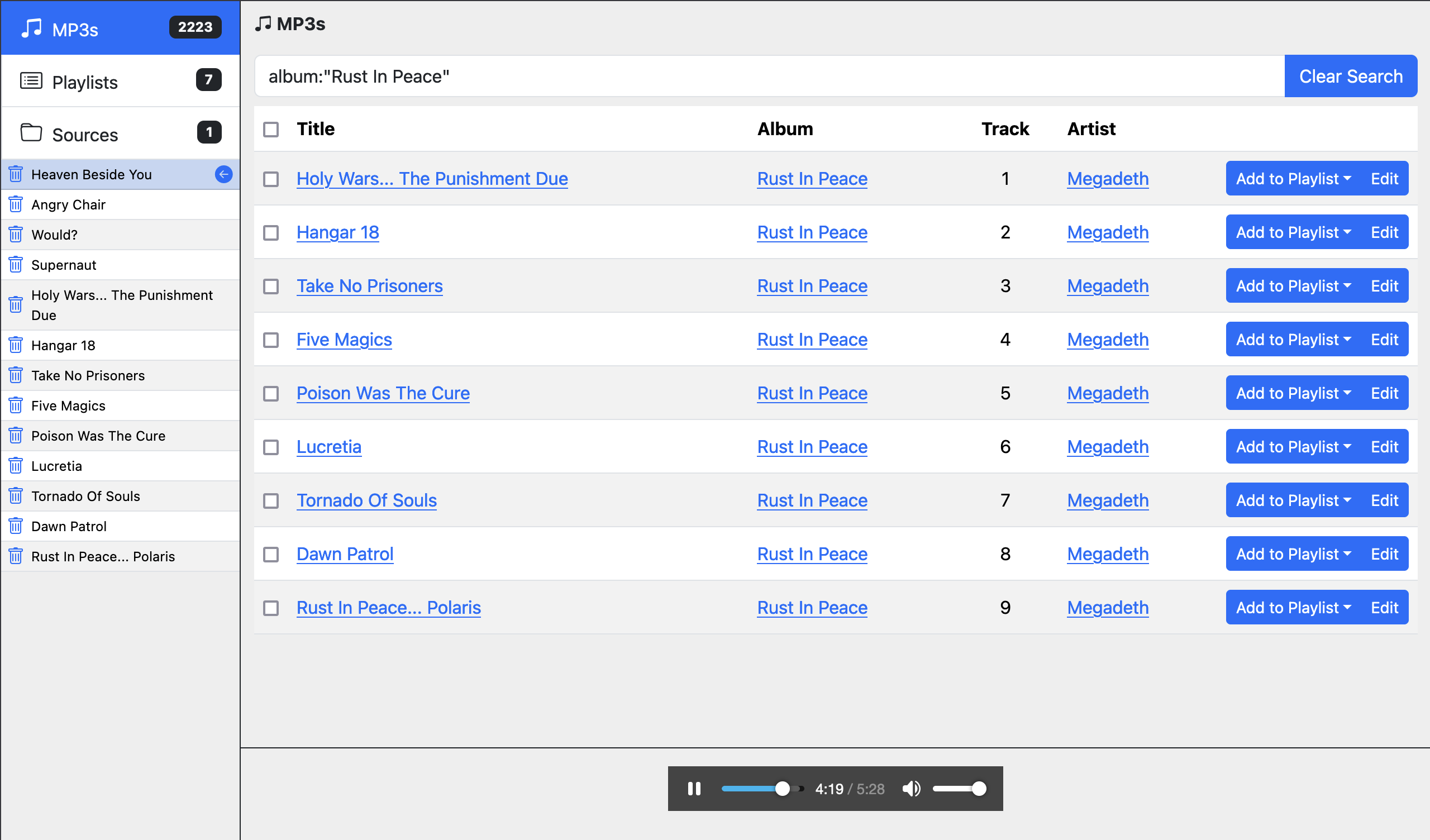
I wrote a simple MP3 player:
https://github.com/gdonald/player
Read More...
ruby (5) rails (4) player (1) mp3 (1)

